Cyber Security Audit Scope

A cyber security audit focuses on cyber security standards guidelines and procedures as well as the implementation of these controls.
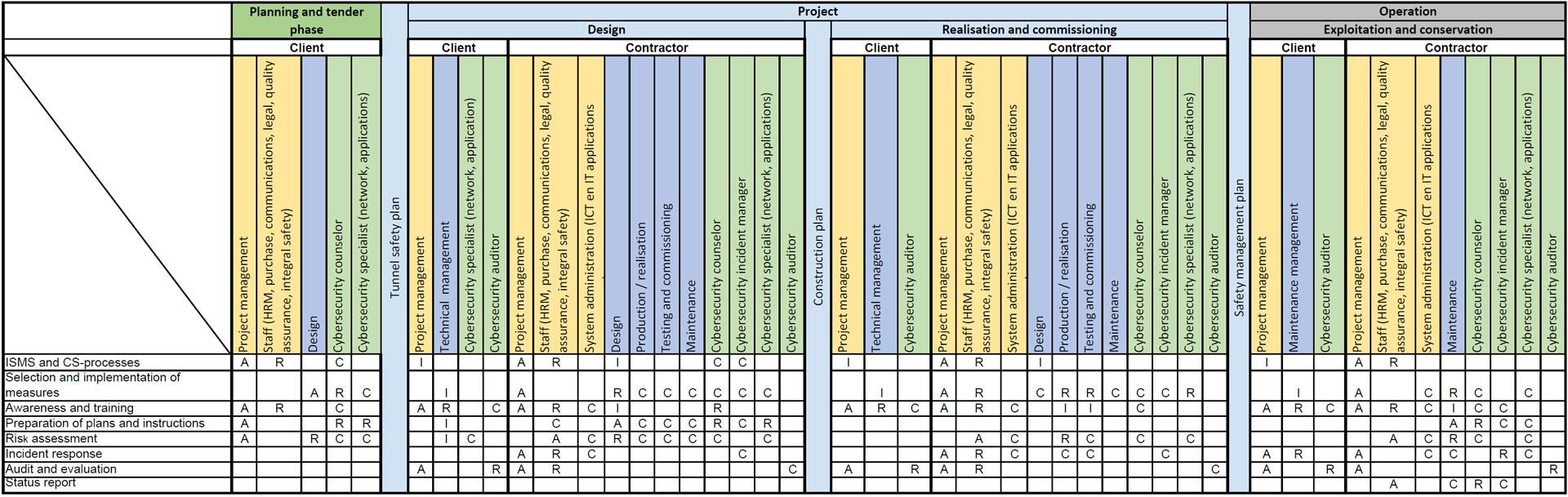
Cyber security audit scope. Companies sometimes question the usefulness of an internal cybersecurity audit and the question of aren t standard risk assessments enough to formulate a security strategy to protect a company s. The audit objectives should be limited to a reasonable scope and should also correspond to cybersecurity and protection goals as defined by the enterprise figure 2. Benefits of cybersecurity audit. Five areas where the security audit process is transformed stage 1 planning scoping and logistics.
The role of the chief audit executive cae related to assurance governance risk and cyber threats. Understand the cyber liability insurance and its impact on cybersecurity. The essential 8 auditor reduces site visits and travel. Exclusively by internal audit.
Many it and security professionals think of a security audit as a stressful expensive solution to assessing the security compliance of their organization it is with external security audit costs hovering in the 50k range. This practice guide discusses the internal audit activity s role in cybersecurity including. Security audit process. It can be difficult to know where to begin but stanfield it have you covered.
And use of analytics and subsequent pressures on data governance create heavy burdens for banks regardless of size and scope of operations. This cyber security audit checklist breaks it all down into manageable queries that you can easily answer. Once the objectives for the audit have been defined the planning and scoping process should identify all areas and aspects of cybersecurity to be covered. Information security in addition to the it function the information security team will often have.
This paper highlights four cybersecurity related industry trends in the technology sector that internal audit teams should consider and whose associated risks those teams might have to confront. The first second and third lines of defense roles and responsibilities related to risk. Learn how to explain and analyze cybersecurity from an audit perspective including the analysis of the scope limitations and evaluation methods. Assessing inherent risks and threats.
A cyber security audit checklist is a valuable tool for when you want to start investigating and evaluating your business s current position on cyber security. Learn how to identify preventive detective and corrective controls. The sbs it audit is risk based and tailored to the size and complexity of each individual organization providing a personalized experience. The ever increasing reliance on technology and the rate at which those technologies change make the inclusion of it audit essential to an effective overall information security program.
The planning part of a security audit will define the objectives scope work activities and logistics. Perspectives into actions that could help audit shops prepare to address cyber risk by building relationships identifying and adapting their role and developing.